下载后是一个流量包,对其进行分析,注意到每次DNS请求前面都是一个8位的字符,猜测可能是bytes内容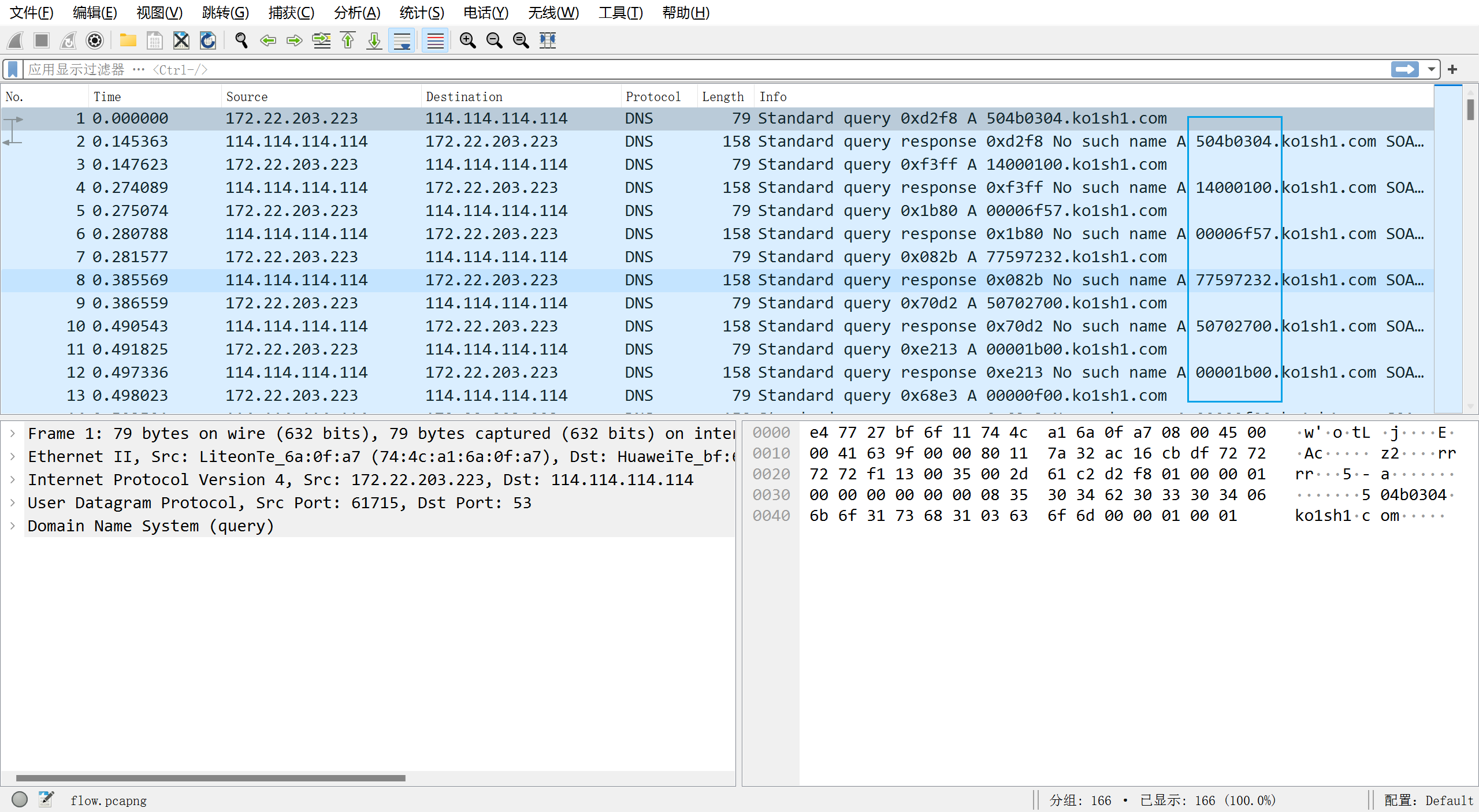
使用tshark将流量包转为json类型tshark -r flow.pcapng -T json > res.json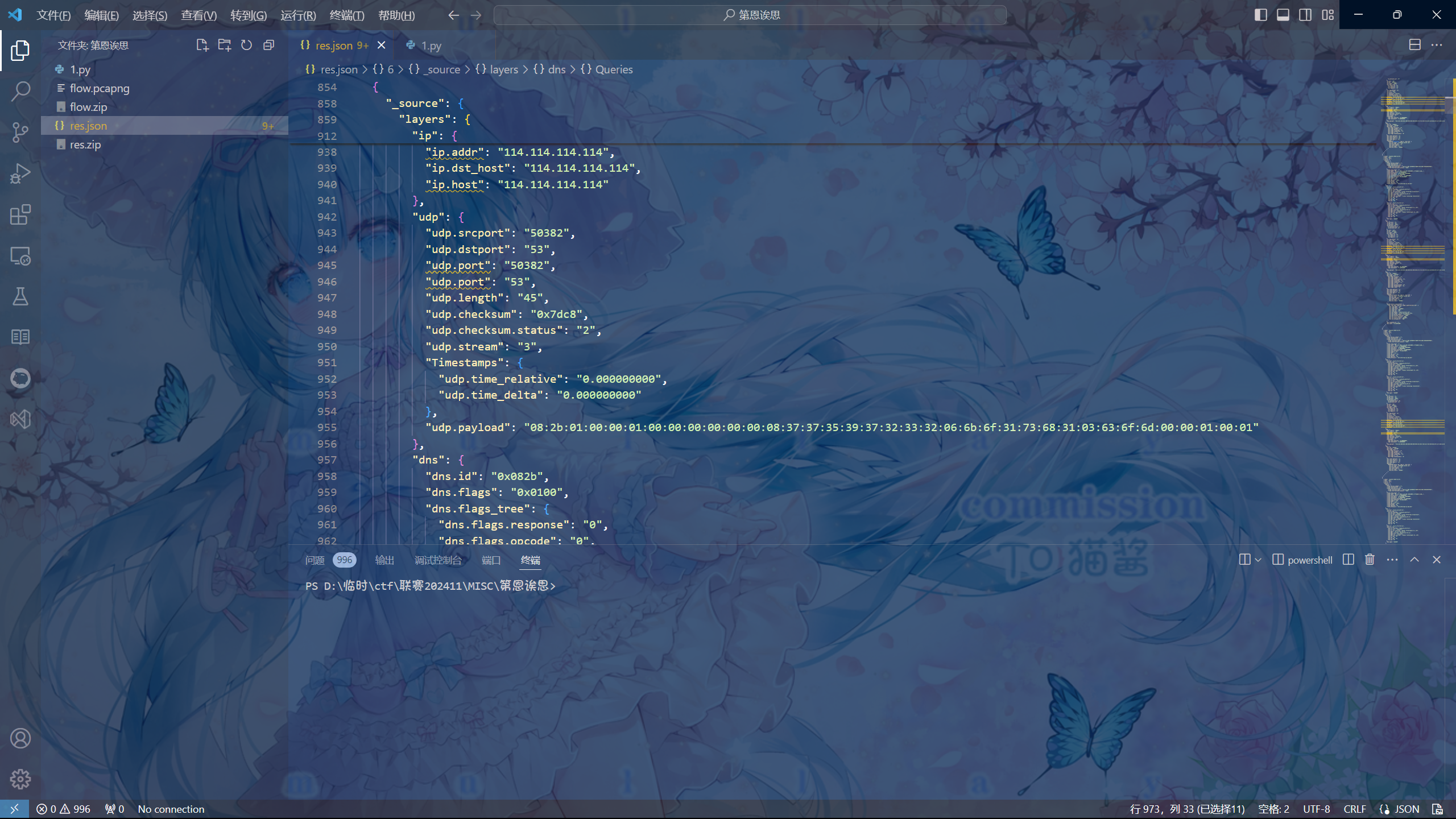
编写脚本读取上面提到的疑似bytes的内容并直接对其进行转换(因WP是做完写的,所以脚本仅展示最终版本),从输出来看有PK(即504B)应该是ZIP压缩包文件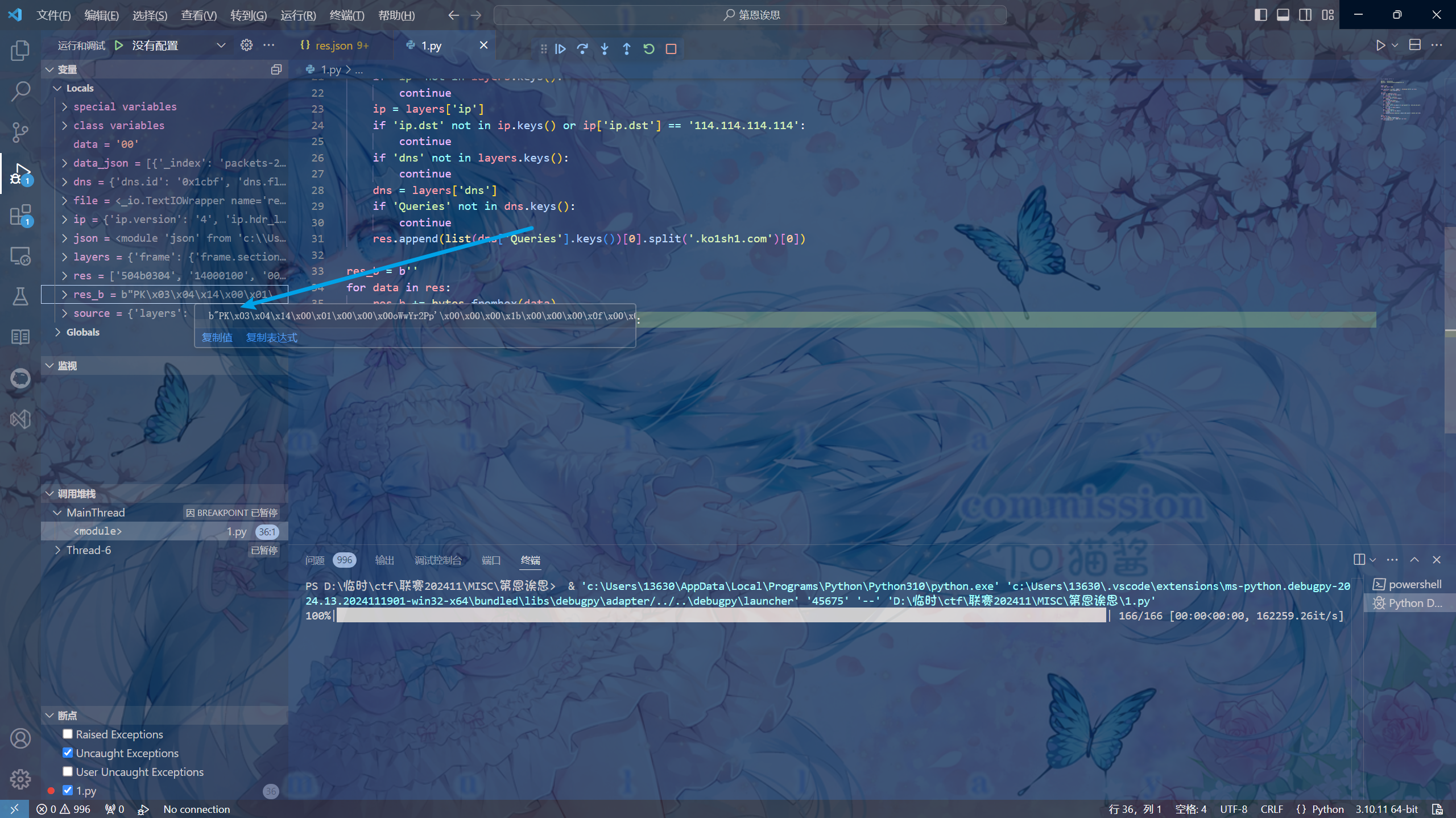
修改脚本直接输出为ZIP压缩包
# -*- coding: utf-8 -*-
'''
@Author : Hatanezumi
@Contact : Hatanezumi@chunshengserver.cn
'''
import json
from tqdm import tqdm
with open('res.json', 'r', encoding='utf-8') as file:
data_json = json.load(file)
res = []
for data in tqdm(data_json):
if '_source' not in data.keys():
continue
source = data['_source']
if 'layers' not in source.keys():
continue
layers = source['layers']
if 'ip' not in layers.keys():
continue
ip = layers['ip']
if 'ip.dst' not in ip.keys() or ip['ip.dst'] == '114.114.114.114':
continue
if 'dns' not in layers.keys():
continue
dns = layers['dns']
if 'Queries' not in dns.keys():
continue
res.append(list(dns['Queries'].keys())[0].split('.ko1sh1.com')[0])
res_b = b''
for data in res:
res_b += bytes.fromhex(data)
with open('res.zip', 'wb') as file:
file.write(res_b)打开压缩包发现有密码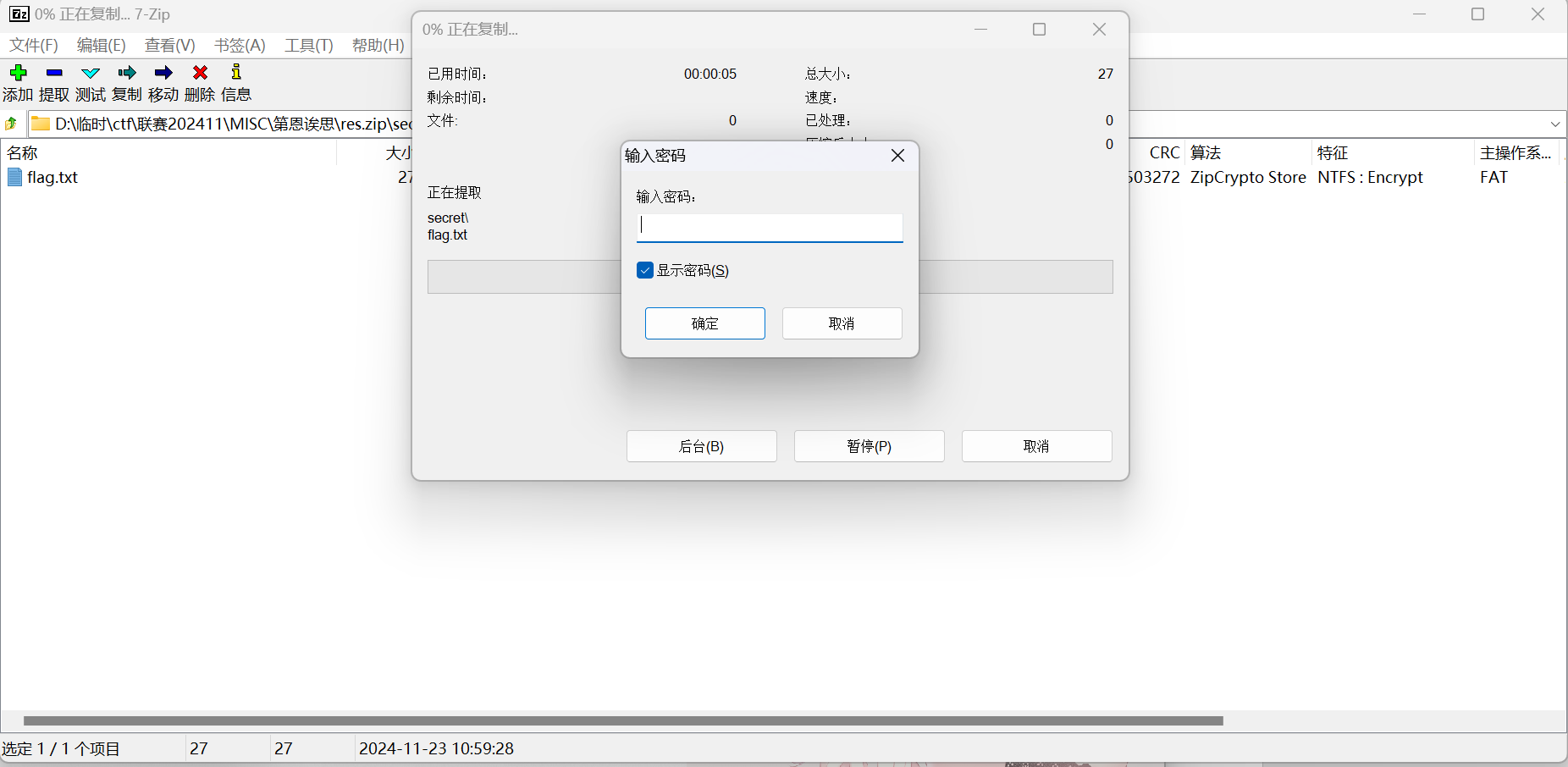
直接使用Advanced-Archive-Password-Recovery-Professional-Edition-master进行爆破,成功得到密码Ab1D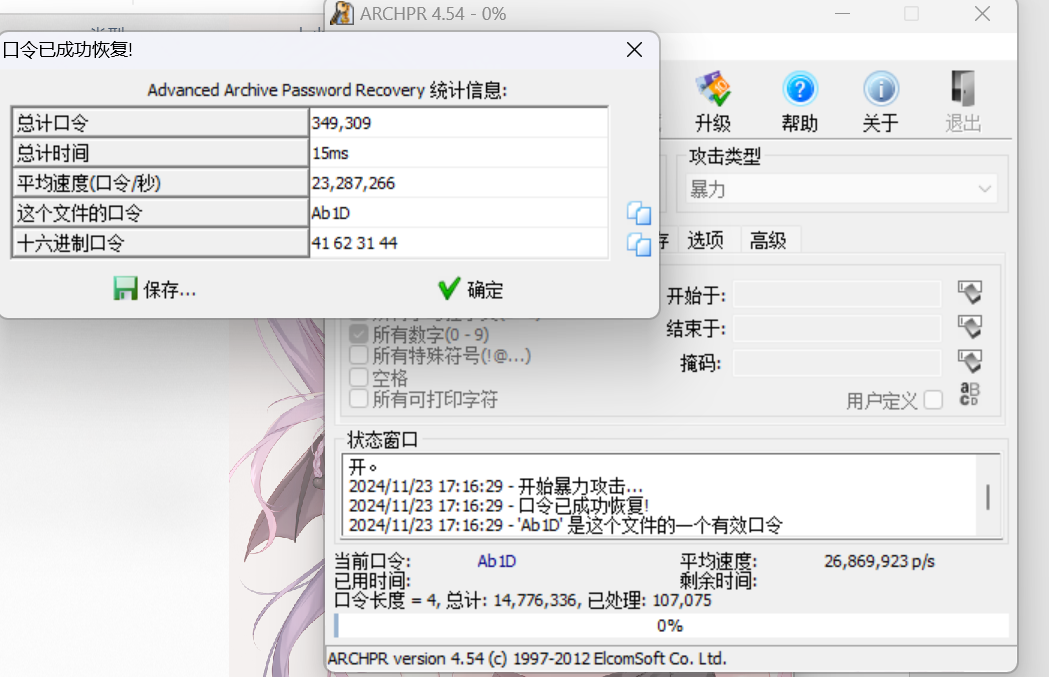
打开压缩包获得flag
flag值:
flag{yOU_FIND_mE!G5UFl11ag}
